符号执行Symcc与模糊测试AFL结合实践

本文为看雪论坛优秀文章
看雪论坛作者ID:FSTARK
背景介绍
1. 模糊测试 AFL
模糊测试(fuzz testing, fuzzing)是一种软件测试技术。其核心思想是将自动或半自动生成的随机数据输入到一个程序中,并监视程序异常,如崩溃、断言(assertion)失败,以发现可能的程序错误,比如内存泄漏。模糊测试常常用于检测软件或计算机系统的安全漏洞。
The goal of this project is to evaluate the robustness of various UNIX utility programs, given an unpredictable input stream. [...] First, you will build a fuzz generator. This is a program that will output a random character stream. Second, you will take the fuzz generator and use it to attack as many UNIX utilities as possible, with the goal of trying to break them.
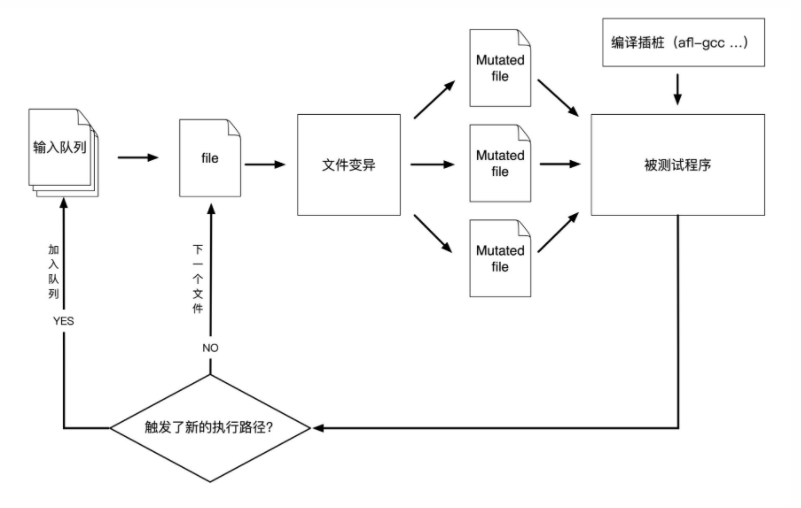
AFL(american fuzzy lop)最初由Michał Zalewski开发,和libFuzzer等一样是基于覆盖引导(Coverage-guided)的模糊测试工具,它通过记录输入样本的代码覆盖率,从而调整输入样本以提高覆盖率,增加发现漏洞的概率。其工作流程大致如下:
(1) 从源码编译程序时进行插桩,以记录代码覆盖率(Code Coverage)
2. 符号执行 Symcc
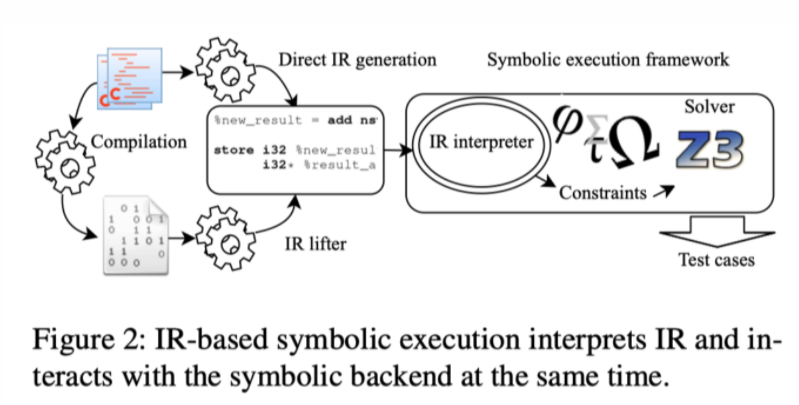

作者提出的SymCC不同点在于,直接在编译期就开始在生成的IR上植入符号执行相关代码,进一步提升性能;其流程大致如下:

开始结合
1. 安装各种环境
sudo apt-get install -y cargo \clang-10 \cmake \g++ \git \libz3-dev \llvm-10-dev \llvm-10-tools \ninja-build \python3-pip \zlib1g-devpip3 install lit
git clone https://github.com/Z3Prover/z3cd z3python scripts/mk_make.pycd buildmakesudo make install
git clone -b v2.56b https://github.com/google/AFL.git aflcd afl && make
git clone https://github.com/eurecom-s3/symcc symcc_sourcecd symcc_sourcegit submodule initgit submodule update
2. 编译backend
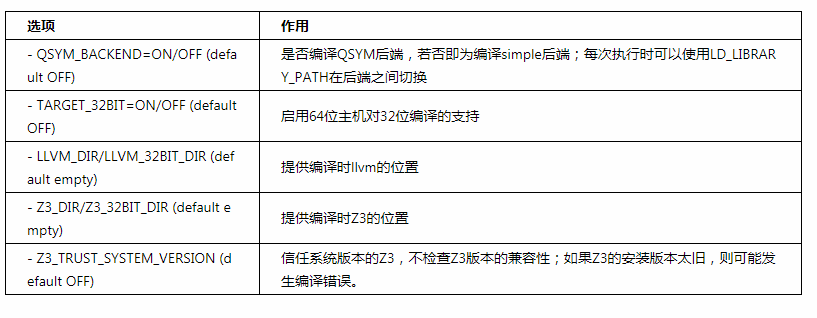
首先编译简单的后端,这里的LLVM_DIR指向你所用版本llvm位置 。
mkdir symcc_build_simplecd symcc_build_simpleCC=clang-10 CXX=clang++-10 cmake -G Ninja \-DQSYM_BACKEND=OFF \-DCMAKE_BUILD_TYPE=RelWithDebInfo \-DZ3_TRUST_SYSTEM_VERSION=on \-DLLVM_DIR=/usr/lib/llvm-10/cmake \../symcc_source \&& ninja check

mkdir symcc_build_qsymcd symcc_build_qsymcmake -G Ninja \-DQSYM_BACKEND=ON \-DCMAKE_BUILD_TYPE=RelWithDebInfo \-DZ3_TRUST_SYSTEM_VERSION=on \-DLLVM_DIR=/usr/lib/llvm-10/cmake \-DZ3_DIR=/home/fstark/symcc_afl/z3/build \../symcc_source \&& ninja check \&& cargo install --path ../symcc_source/util/symcc_fuzzing_helper

3. 用symcc编译llvm的libcxx
编译过程如下:
git clone -b llvmorg-10.0.1 --depth 1 https://github.com/llvm/llvm-project.git llvm_sourcemkdir libcxx_symcc_installmkdir libcxx_symcc_buildcd libcxx_symcc_buildexport SYMCC_REGULAR_LIBCXX=yes SYMCC_NO_SYMBOLIC_INPUT=yes \&& cmake -G Ninja ../llvm_source/llvm \-DLLVM_ENABLE_PROJECTS="libcxx;libcxxabi" \-DLLVM_TARGETS_TO_BUILD="X86" \-DLLVM_DISTRIBUTION_COMPONENTS="cxx;cxxabi;cxx-headers" \-DCMAKE_BUILD_TYPE=Release \-DCMAKE_INSTALL_PREFIX=$BASE/libcxx_symcc_install \-DCMAKE_C_COMPILER=$BASE/symcc_build_simple/symcc \-DCMAKE_CXX_COMPILER=$BASE/symcc_build_simple/sym++ \&& ninja distribution && ninja install-distribution

4. 开始尝试Fuzz!
#include <stdio.h>#include <stdint.h>#include <unistd.h>#include <string.h>#include <stdlib.h>int foo(char *arr, int t1){int i = 0;if (arr[i++] == 'c') return 0;if (arr[i++] == 'd') return 1;if (arr[i++] == 'c') return 2;if (arr[i++] == 'c') return 3;if (arr[i++] == 's') return 4;if (arr[i++] == 'b') return 5;if (arr[i++] == 's') return 6;if (arr[i++] == 'g') return 7;if (*(int*)arr != 0xdeadbeef )return 0;//Can we trigger this code?return (int)(20 / t1);}int main(int argc, char* argv[]){//open fileFILE *f = fopen(argv[1],"rb");// get file sizefseek(f, 0, SEEK_END);long fsize = ftell(f);// read file contentsfseek(f, 0, SEEK_SET);char *string = malloc(fsize + 1);fread(string, 1, fsize, f);fclose(f);// pass string to fooint retval = foo(string, argc-2);free(string);return retval;}
afl-clang -O0 int_check.c -o afl_int_check../symcc_build_qsym/symcc -O0 int_check.c -o symcc_int_checkmkdir corpusecho "AAAAAAAAAAAAAAAAAAAAAAAA" > corpus/seed
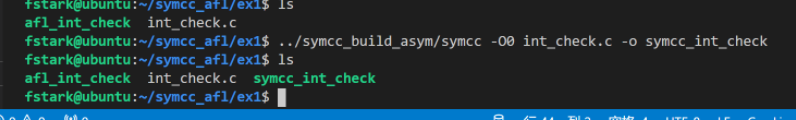
afl-fuzz -M fuzz1 -i corpus/ -o out -m none -- ./afl_int_check @@afl-fuzz -S fuzz2 -i corpus/ -o out -m none -- ./afl_int_check @@~/.cargo/bin/symcc_fuzzing_helper -o out -a fuzz2 -n symcc -- ./symcc_int_check @@


总结

参考资料
https://github.com/eurecom-s3/symcc/


看雪ID:FSTARK
https://bbs.pediy.com/user-home-832012.htm
# 往期推荐

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
- 12306抢票不是先到先得!优先满足始发站到终到站的长途旅客
- 为什么欧洲无法创建能够与 Android 和 iOS 抗衡的移动操作系统?
- 高端掘金局?这座矿山有点儿东西!
- 打牢智能根基,加速行业升级
- 直播预告|后疫情时代下对安全风控的思考与碰撞
- 百度一高级经理因违反竞业协议被判赔107万;苹果、谷歌和微软扩大对无密码登陆的支持;Firefox 100 发布|极客头条
- 惊喜不断,福利多多,云盲盒的快乐等你来开!
- Linux 新漏洞曝光,居然又双叒是提升权限漏洞!
- Linux 内核支持 Rust;中科院计划每半年升级一次 RISC-V 芯片;Python 3.10.1 发布 | 开源日报
- C 和 Java 没那么香了,Serverless 时代 Rust 即将称王?
- 大量数据丢失且无法恢复!欧洲云服务巨头数据中心起火
- 云时代下,移动云揭秘数据库“新解”