大杀器Unidbg真正的威力
看雪论坛作者ID:至尊小仙侠
论2021如何处理 arm vmp?
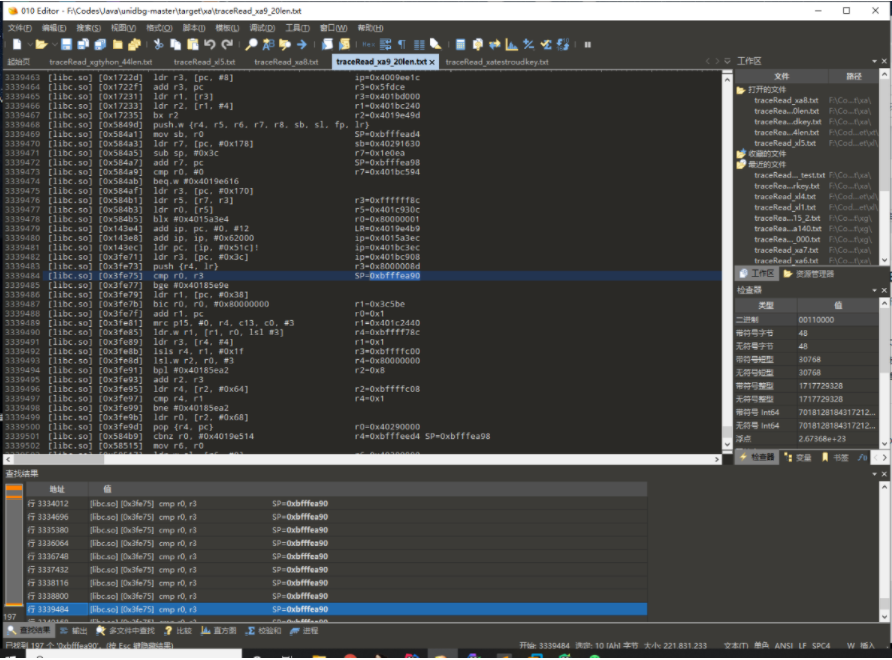
有图有真相 Unidbg的杀手锏 CPU指令级别Trace
callFunction:
那么我们在分析So的过程中,发现了一个非JNI函数能不能主动调用呢?答案是必须能。

public final Number[] callFunction(Emulator<?> emulator, String symbolName, Object... args) {Symbol symbol = findSymbolByName(symbolName, false);if (symbol == null) {throw new IllegalStateException("find symbol failed: " + symbolName);}if (symbol.isUndef()) {throw new IllegalStateException(symbolName + " is NOT defined");}return symbol.call(emulator, args);}
emulator = createARMEmulator();
private static void CallVMPFunc(Module module,AndroidEmulator emulator){try {Symbol malloc = module.findSymbolByName("malloc");Symbol free = module.findSymbolByName("free");MemoryBlock block = MemoryAllocBlock.malloc(emulator,malloc,free,0x1000);MemoryBlock namebyte = MemoryAllocBlock.malloc(emulator,malloc,free,0x1000);UnidbgPointer blockpoint = block.getPointer();UnidbgPointer namepoint = namebyte.getPointer();String name = "magicillusion";String data = "hello worid";namepoint.write(name.getBytes());blockpoint.write(data.getBytes());Number[] ret = module.callFunction(emulator,0x13B30+1,namepoint,blockpoint,2);UnidbgPointer ret1 = new UnidbgPointer(emulator,ret[0].intValue(),4);String string = ret1.getString(0);System.out.println("Number => " + (string));} finally {}}
大杀器内置的HOOK框架
// 1. 获取HookZz对象IHookZz hookZz = HookZz.getInstance(emulator); // 加载HookZz,支持inline hook,文档看https://github.com/jmpews/HookZz// 2. enable hookhookZz.enable_arm_arm64_b_branch(); // 测试enable_arm_arm64_b_branch,可有可无index = 0;hookZz.replace(module.findSymbolByName("lrand48"), new ReplaceCallback() {@Overridepublic void postCall(Emulator<?> emulator, HookContext context) {((EditableArm32RegisterContext)context).setR0(0x12345678);int ptrace_args0 = context.getIntArg(0);System.out.println("lrand48=" + ptrace_args0);}},true);//aesdecode hookhookZz.wrap((module.base)+0x39634+1, new WrapCallback<RegisterContext>() { // inline wrap导出函数UnidbgPointer addr = null;@Override// 4. 方法执行前public void preCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {addr= ctx.getPointerArg(0);UnidbgPointer pointerArg = ctx.getPointerArg(1);UnidbgPointer pointer = pointerArg.getPointer(12);int anInt = pointerArg.getInt(8);byte[] byteArray = pointer.getByteArray(0, anInt);String s =xuzi1(byteArray);System.out.println("aes aesdecode= " + s);}@Override// 5. 方法执行后public void postCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {byte[] aaaa = addr.getPointer(0).getPointer(12).getByteArray(0,0x30);String s =xuzi1(aaaa);System.out.println("aes aesdecode1= " + s);}});

看雪ID:至尊小仙侠
https://bbs.pediy.com/user-home-873999.htm

官网:https://www.bagevent.com/event/6334937

# 往期推荐
2. CVE-2021-26708 利用四字节释放特定地址,修改内存
3.网刃杯逆向wp

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/

 关注KnowSafe微信公众号
关注KnowSafe微信公众号