『直播中』从unidbg trace log中还原被ollvm混淆的非标准算法
看雪会员『至尊小仙侠』写的《大杀器Unidbg真正的威力》让我们认识到Unidbg强大,今天我们一起回顾一下吧
论2021如何处理 arm vmp?
有图有真相 Unidbg的杀手锏 CPU指令级别Trace

callFunction:
那么我们在分析So的过程中,发现了一个非JNI函数能不能主动调用呢?答案是必须能。
public final Number[] callFunction(Emulator<?> emulator, String symbolName, Object... args) {Symbol symbol = findSymbolByName(symbolName, false);if (symbol == null) {throw new IllegalStateException("find symbol failed: " + symbolName);}if (symbol.isUndef()) {throw new IllegalStateException(symbolName + " is NOT defined");}return symbol.call(emulator, args);}
emulator = createARMEmulator();
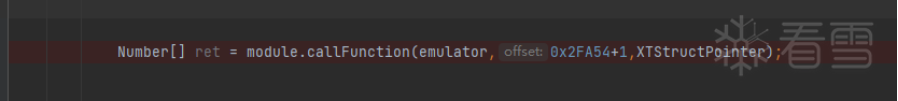
private static void CallVMPFunc(Module module,AndroidEmulator emulator){try {Symbol malloc = module.findSymbolByName("malloc");Symbol free = module.findSymbolByName("free");MemoryBlock block = MemoryAllocBlock.malloc(emulator,malloc,free,0x1000);MemoryBlock namebyte = MemoryAllocBlock.malloc(emulator,malloc,free,0x1000);UnidbgPointer blockpoint = block.getPointer();UnidbgPointer namepoint = namebyte.getPointer();String name = "magicillusion";String data = "hello worid";namepoint.write(name.getBytes());blockpoint.write(data.getBytes());Number[] ret = module.callFunction(emulator,0x13B30+1,namepoint,blockpoint,2);UnidbgPointer ret1 = new UnidbgPointer(emulator,ret[0].intValue(),4);String string = ret1.getString(0);System.out.println("Number => " + (string));} finally {}}
大杀器内置的HOOK框架
// 1. 获取HookZz对象IHookZz hookZz = HookZz.getInstance(emulator); // 加载HookZz,支持inline hook,文档看https://github.com/jmpews/HookZz// 2. enable hookhookZz.enable_arm_arm64_b_branch(); // 测试enable_arm_arm64_b_branch,可有可无index = 0;hookZz.replace(module.findSymbolByName("lrand48"), new ReplaceCallback() {@Overridepublic void postCall(Emulator<?> emulator, HookContext context) {((EditableArm32RegisterContext)context).setR0(0x12345678);int ptrace_args0 = context.getIntArg(0);System.out.println("lrand48=" + ptrace_args0);}},true);//aesdecode hookhookZz.wrap((module.base)+0x39634+1, new WrapCallback<RegisterContext>() { // inline wrap导出函数UnidbgPointer addr = null;@Override// 4. 方法执行前public void preCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {addr= ctx.getPointerArg(0);UnidbgPointer pointerArg = ctx.getPointerArg(1);UnidbgPointer pointer = pointerArg.getPointer(12);int anInt = pointerArg.getInt(8);byte[] byteArray = pointer.getByteArray(0, anInt);String s =xuzi1(byteArray);System.out.println("aes aesdecode= " + s);}@Override// 5. 方法执行后public void postCall(Emulator<?> emulator, RegisterContext ctx, HookEntryInfo info) {byte[] aaaa = addr.getPointer(0).getPointer(12).getByteArray(0,0x30);String s =xuzi1(aaaa);System.out.println("aes aesdecode1= " + s);}});






# 往期推荐
2. NtSockets - 直接与驱动通信实现sockets
4. CVE-2022-0995分析(内核越界 watch_queue_set_filter)
球分享

球点赞

球在看

点击“阅读原文”,了解更多!
[广告]赞助链接:
关注数据与安全,洞悉企业级服务市场:https://www.ijiandao.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注KnowSafe微信公众号
关注KnowSafe微信公众号随时掌握互联网精彩
- LANDrop开源免费的跨平台文件传输工具
- 伊朗切断全国互联网和电话通信服务应对网络攻击 互联网流量跌至平时的3%
- 乌克兰黑客渗透到俄罗斯网络提供商Nodex后将其所有数据全部清空
- PrimeVue:引领潮流 下一代 Vue UI 组件库
- 数篷观察:数据安全八大发展趋势
- 心向远方 携手奔赴山海
- 历史上的今天:Linux 开发的“二把手”出生;苹果发布 OS 8;MSN 发布
- 关于八方教育在“直播课程”中碰瓷营销的公开声明
- 历史上的今天:Java 之父诞生;中国首家互联网公司成立;CP/M 操作系统发明者出生
- 物联网安全漏洞实战,全方位解析IoT安全!
- Wi-Fi 6 增强版为何成为今年的旗舰标配?丨骁龙问答室
- SSL证书太贵了?与未部署SSL证书潜在的损失比真不贵!
赞助链接